Phishing scams have become one of the most prevalent and dangerous forms of cybercrime. These deceptive tactics are designed to trick individuals and businesses into revealing sensitive information—such as login credentials, bank details, or personal data—by impersonating legitimate organisations.
While phishing attempts can take many forms, email remains the most common method used by cybercriminals. According to recent cybersecurity reports, over 3.4 billion phishing emails are sent daily. Studies show that approximately 32% of data breaches involve phishing tactics, highlighting the critical importance of being able to identify these threats.
This guide will walk you through 10 effective strategies to help you detect phishing email addresses, highlight common phishing tactics to be aware of, and provide clear steps to take if you believe you've been targeted.
Understanding Phishing Scams
Phishing scams are fraudulent attempts to obtain sensitive information by disguising as a trustworthy entity. Before examining specific detection techniques, it's important to understand how these scams operate and the forms they take.
What is a Phishing Scam?
A phishing scam is a type of cybercrime where attackers impersonate legitimate organisations to trick victims into revealing sensitive information. These scams typically involve deceptive communications that appear to come from trusted sources such as banks, government agencies, or popular online services.
The ultimate goal of a phishing scam is to steal credentials, financial information, or personal data that can be used for identity theft, financial fraud, or unauthorised account access.
How Phishing Scams Work
Phishing scams operate by creating a false sense of legitimacy and often urgency. Attackers send fraudulent messages containing suspicious links or attachments that, when interacted with, can install malware or redirect users to fraudulent websites designed to steal information.
Scammers employ social engineering tactics, creating a sense of urgency or fear to pressure victims into acting quickly—such as claiming that an account will be suspended unless details are verified immediately.
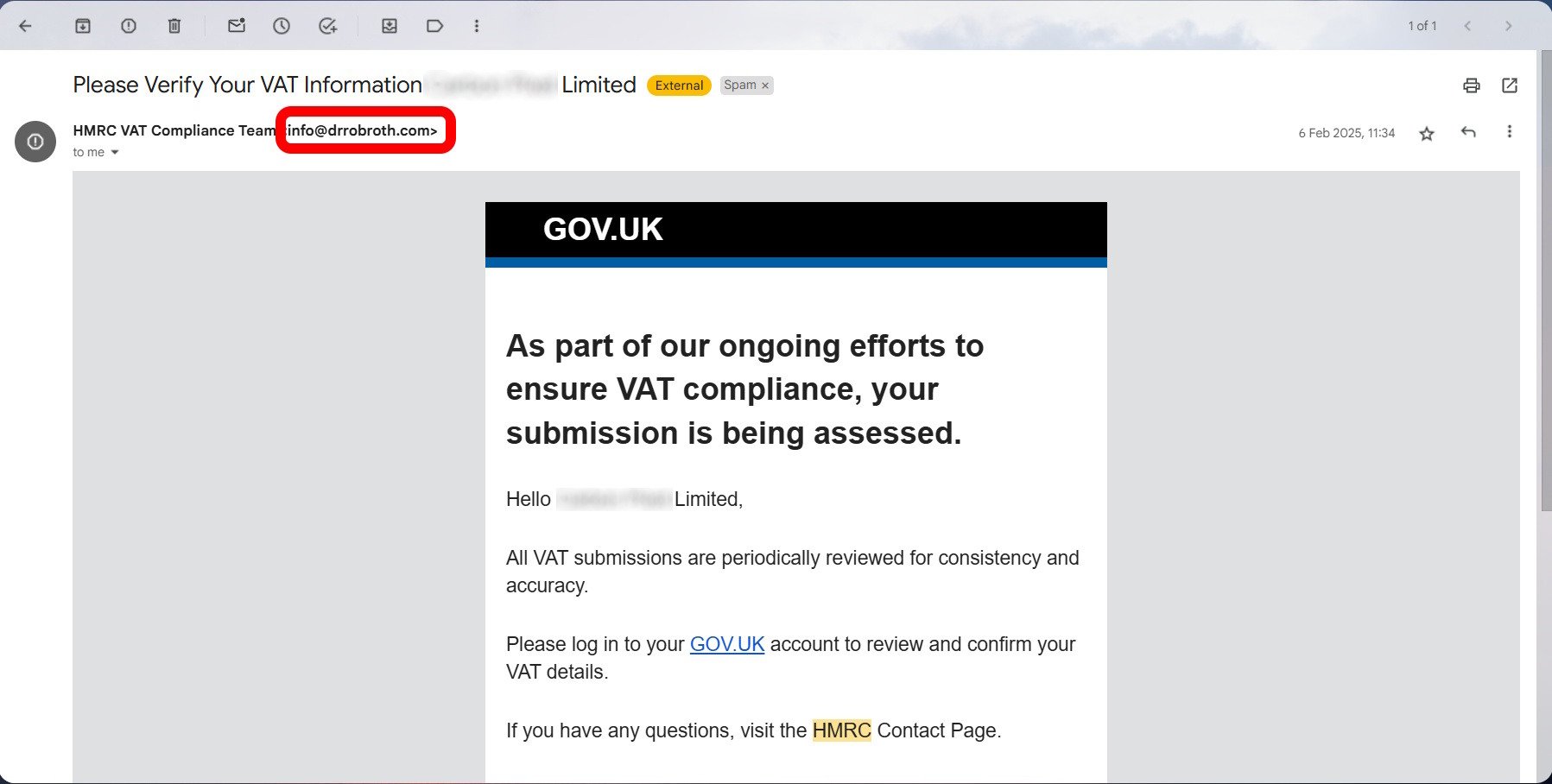
What is a Phishing Website?
A phishing website is a fraudulent site designed to imitate a legitimate one, such as an online banking platform, e-commerce site, or popular social media network. These sites are crafted to look authentic and trick users into entering sensitive information like login credentials, credit card details, or personal data. Once entered, this information is captured by scammers for malicious use.
Types of Phishing Scams
Phishing attacks can take various forms, targeting individuals or specific industries:
- Email Phishing: The most common form, where attackers impersonate legitimate entities
- Phone Phishing (Vishing): Scammers use phone calls to deceive victims into sharing sensitive information
- Text Message Phishing (Smishing): Fraudulent messages encourage users to click malicious links or share personal data
- Spear Phishing: Targeted attacks aimed at specific individuals or organisations, using personalised information
- Clone Phishing: A legitimate email is duplicated with malicious links inserted
- Business Email Compromise (BEC): Attackers impersonate executives to request fraudulent wire transfers or data
- AI-Generated Phishing: Emerging threat using artificial intelligence to create highly convincing fake communications
Phishing scams can also extend to fake social media profiles or fraudulent websites designed to steal user data by impersonating trusted brands.
Identifying Fake Email Addresses
Phishing emails are often crafted to appear legitimate, making them difficult to spot at first glance from genuine emails. However, by carefully analysing the email address itself, you can uncover the tell-tale signs of a scam. Here are our 10 effective ways to detect phishing email addresses and protect yourself from falling victim to cybercriminals.
1. Check for Suspicious Sender Email Addresses
The first red flag is the sender’s email address. Scammers often create addresses that look legitimate at first glance but contain small inconsistencies. Be cautious of:
- Random characters or numbers in the email address (e.g., support123@banking-secure.com).
- Unicode tricks, where similar-looking characters are swapped to deceive (e.g., using "ɑ" instead of "a").
- Misspellings in familiar brand names (e.g., cust0mer@amaz0n.co.uk).
2. Look for Misspelt or Imitated Domain Names
Scammers often create fake domains that look almost identical to real ones. Check the domain carefully for:
- Subtle misspellings (e.g., micorsoft.com instead of microsoft.com)
- Slight variations of familiar domains (e.g., secure-paypal.com instead of paypal.com)
- Strange or unexpected domain endings (e.g., .net or .org instead of .co.uk or .com)
3. Verify the Sender’s Display Name
Phishers often disguise their email address with a familiar display name. Always check if the email address matches the display name. For example, an email from "Amazon Support" using the address amazonhelpdesk@gmail.com is suspicious.
4. Be Wary of Public Email Domains for Business Communications
Legitimate companies rarely use free, public email providers like Gmail, Yahoo, or Outlook for official communication. An email from a business should come from a corporate domain (e.g., @paypal.com, not @gmail.com).
5. Analyse Unusual or Complex Email Structures
Professional companies use clear, concise email addresses. If an email looks unnecessarily complicated (e.g., sales-team-department-456@official-check.net), it could be a phishing attempt.
6. Check for Email Address Mismatches
Sometimes, scammers use a legitimate-looking domain but send from an unrelated address. Compare the "From" email address with the "Reply-To" address—if they don’t match, it could be a phishing attempt.
7. Spot Suspicious Subdomains
Phishers may use subdomains to appear legitimate (e.g., paypal.securelogin.com). Always focus on the main domain; in this case, the real domain is paypal.com/signin.
8. Hover Over Links Without Clicking
Phishing emails often contain links disguised as legitimate URLs. Hover your cursor over any links in the email (without clicking) to reveal the true destination. If the link doesn’t match the supposed sender’s website, it’s likely a scam.
9. Examine Email Headers
For advanced protection, learn to check email headers. Email headers contain detailed information about the sender's server and the path the email took to reach you. Most email clients allow you to view the full headers, where you can verify the sending server's IP address and check if it matches known servers for the organisation.
10. Verify the Email Through Official Channels
When in doubt, contact the organisation directly using official contact information from their website—never use contact details provided in the suspicious email.
Additional Red Flags in Phishing Emails
While the email address is a strong indicator of phishing, be aware of other common tactics scammers use:
- Urgent or threatening language: Scammers often create a sense of urgency (e.g., "Your account will be suspended unless you act now!")
- Requests for sensitive information: Legitimate companies will never ask for account credentials, credit card numbers, or personal details via email
- Unexpected attachments: Phishing emails may carry malicious attachments designed to install malware or steal information
- Too-good-to-be-true offers: If an offer seems too good to be true, it likely is
- Inconsistent formatting or branding: Poor quality logos, unusual fonts, or layout issues can indicate a fake email
Recognising Common Phishing Tactics
In addition to spotting suspicious email addresses, scammers often use familiar tactics to trick victims into clicking malicious links or revealing sensitive information. Here are some common phishing scams to watch out for:
- Phony Parcel Delivery Notices: Emails claiming to be from courier services like Royal Mail or DPD, often asking for payment or prompting you to click a link to reschedule delivery
- 'Too Good to Be True' Offers: Scammers promise rewards, prizes, or unexpected financial gains to lure victims into providing sensitive information
- Targeted Industry Scams: Certain phishing attacks focus on specific industries or groups, using relevant language or references to appear credible
- Suspicious URLs: Be wary of emails urging you to click links. Always hover over links first to reveal the actual destination
- Malicious Attachments: Attachments from unknown senders may contain malware or viruses intended to compromise your device
Emerging Phishing Threats
As technology evolves, so do phishing techniques. Be aware of these newer threats:
- AI-Generated Content: Attackers now use artificial intelligence to create highly convincing phishing emails with fewer grammatical errors and more persuasive language
- QR Code Phishing: Fraudulent QR codes that direct users to malicious websites when scanned
- Multi-Platform Attacks: Coordinated attempts that combine email phishing with follow-up phone calls or text messages to increase credibility
- Voice Cloning: Using AI to clone voices for vishing (voice phishing) attacks, particularly targeting businesses
- Supply Chain Attacks: Phishing attempts that impersonate vendors or suppliers to target businesses
What to Do If You've Been Scammed
Even with the best precautions, phishing scams can sometimes succeed. If you suspect that you've been targeted, taking immediate action can help limit the damage and protect your sensitive information.
1. Report Email Scams
Reporting phishing emails helps protect others and assists cybersecurity authorities in taking action against scammers. Here's how to report phishing in some major countries:
- United Kingdom: Forward suspicious emails to the National Cyber Security Centre (NCSC) at report@phishing.gov.uk
- United States: Forward phishing emails to the Anti-Phishing Working Group at reportphishing@apwg.org and the Federal Trade Commission (FTC) at reportfraud.ftc.gov
- Australia: Report phishing emails to the Australian Cyber Security Centre (ACSC) via reportcyber.gov.au
- Canada: Report phishing attempts to the Canadian Centre for Cyber Security via phishing@cyber.gc.ca
You should also report phishing emails directly to your email provider by marking the message as phishing or spam, and notify your organisation's IT department if the email was received at work.
2. Take Immediate Action if You've Clicked on a Link
If you've accidentally clicked a suspicious link or downloaded an attachment, act quickly to limit any potential damage:
- Disconnect from the internet temporarily to prevent further data breaches
- Run a full virus and malware scan using trusted security software
- Change your passwords immediately, focusing on sensitive accounts like banking, email, and work-related platforms
- Monitor your accounts for suspicious activity
3. Change Passwords and Monitor Accounts
Once the immediate threat is managed, strengthen your security by:
- Updating passwords for all important accounts, using strong and unique combinations
- Enabling two-factor authentication (2FA) for additional protection
- Monitoring your accounts regularly for suspicious activity, especially financial or sensitive accounts
- Consider using a password manager to maintain unique, complex passwords for each service
Helpful Tools for Phishing Protection
Consider using these tools to provide a comprehensive solution to protect against phishing:
- Email filtering services: Services like Google Workspace and Microsoft 365 have built-in phishing protection
- Password managers: Tools like LastPass, 1Password, or Bitwarden help create and store unique passwords
- Two-factor authentication apps: Google Authenticator, Microsoft Authenticator, or Authy add an extra layer of security
- Anti-phishing browser extensions: Tools that can identify and block phishing websites
- Email header analysers: Online tools that help examine email headers for suspicious indicators
Conclusion
Phishing scams are becoming increasingly sophisticated, making it essential to stay vigilant and proactive in protecting your sensitive information. Learning how to detect suspicious email addresses and recognising common scam tactics can significantly reduce your risk of falling victim to cybercriminals.
If you believe you've been targeted, taking immediate action is critical. Report phishing attempts to the appropriate authorities in your country, run a full security scan, and update your passwords. Implementing security measures such as two-factor authentication and regularly monitoring your accounts can also help safeguard your personal and financial information.
By staying informed, verifying email authenticity, and knowing how to respond if you've been scammed, you can build strong defences against phishing attacks—helping protect not just your data but your peace of mind.




